
Cyber Security & IT Insights
Expert insights from our team to help you secure and scale your business.

Cyber Checklist for Overseas Travel
If your business uses a cyber security policy known as Conditional Access, signing into your Microsoft 365 account from overseas might not work.

Microsoft Edge now blocks ‘Scareware’
Microsoft Edge now has a scareware blocker feature turned on by default.

New ACSC Guidance for AI Security
Using AI tools in your business? The Australian Cyber Security Centre just released critical guidance for business owners.

ASD 2024-25 Cyber Threat Report: What it means for your business
The Australian Signals Directorate has just released its Annual Cyber Threat Report, and the message is clear: cyber threats are still rising, and small businesses remain a prime target.

Australian banking passwords stolen by silent malware
Infostealer — the silent malware harvesting Australians passwords.

Windows 10 is nearing end of support
Microsoft is ending Windows 10 Support on October 14 2025.


Why Your Business Needs an IT Policy
An IT policy provides your employees with clear guidelines for using technology, while addressing the challenges of emerging tools like AI.

Passkeys: The future of smart passwords
Passkeys offer a more secure and user-friendly alternative for online authentication. So what are they?

Australia's new Cyber Security Bill: what's in it?
The Albanese government recently proposed long-awaited legislation aimed at strengthening the nation's cybersecurity defences.

What is an Attack Surface?
Protect your business from cyber threats by managing your Attack Surface.

Cyber security fundamentals: Are you covering the basics?
Company directors have a responsibility to manage cyber security risk. But where do they start?

Who is responsible for cyber security in a business?
Understanding the roles and responsibilities of cyber security in a business.

Australian 2030 Cyber Security Strategy: What it means for businesses
Implementing the six cyber shields to keep businesses and individuals safe.
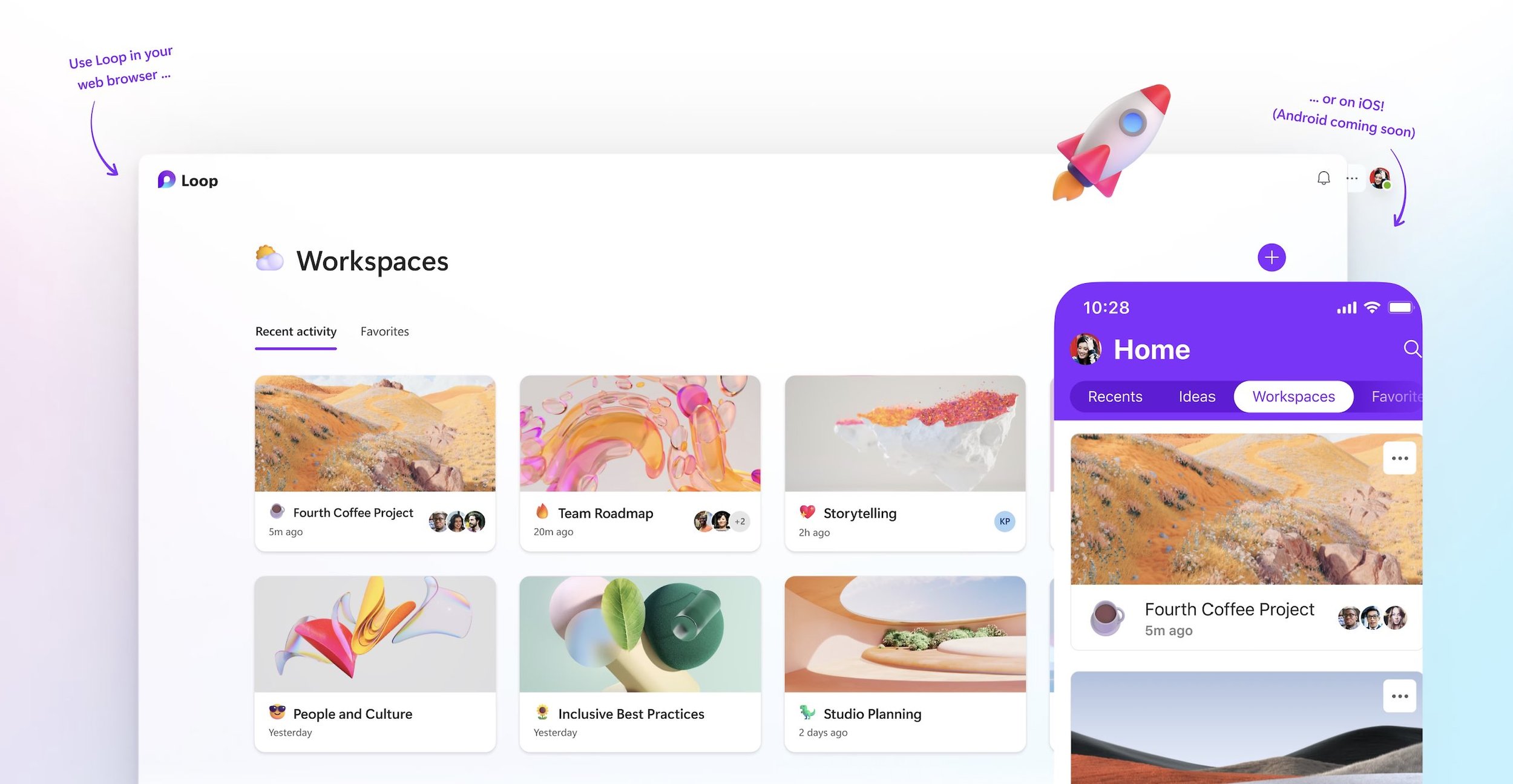
Enhance Collaboration with Microsoft Loop
Microsofts new productivity app is now available for 365 users.

How To Spot a Social Engineering Scam
3 Steps to recognise a Social Engineered Scam targeting your business.

Q&A with James: Your Cyber Questions Answered
Autumn 2023 edition: James Bartrop, CEO of ShadowSafe answers your questions.

Strengthen Security with Conditional Access
How to implement access control for critical accounts and systems.

Information regarding the recent Optus cyberattack
Please read if you’re a current or former Optus customer.

Human Risk Management: What it is and why it matters
The new class of user-focused security that increases resilience to sophisticated phishing attacks.
